Difference between revisions of "Security and Best Practice"
(Created page with "centre The system has a host of security features as standard with a wide range of additional options. On this page you will find details of fe...") |
|||
| Line 1: | Line 1: | ||
| − | [[File:helpheader_small.png| | + | [[File:helpheader_small.png|right]] |
The system has a host of security features as standard with a wide range of additional options. On this page you will find details of features and guides to make you system even more secure. | The system has a host of security features as standard with a wide range of additional options. On this page you will find details of features and guides to make you system even more secure. | ||
| Line 6: | Line 6: | ||
In this section you will find features related to the general access of the system. | In this section you will find features related to the general access of the system. | ||
| − | == | + | ==User name rules== |
'''This feature is planned to be replaced with the use of email addresses for users.''' | '''This feature is planned to be replaced with the use of email addresses for users.''' | ||
| Line 14: | Line 14: | ||
To use this feature please see [[Operational Rules#Security Rules - Usernames|Operational Rules]]. | To use this feature please see [[Operational Rules#Security Rules - Usernames|Operational Rules]]. | ||
| + | |||
| + | ==Password rules== | ||
| + | The system can force users to use secure complex passwords. This will reduce chance of passwords being guessed by unauthorised people. Password rules are also used to protect against 'Brute Force Attacks' (when a combination of characters for the user name and password are entered until access is granted). | ||
| + | |||
| + | The following rules are available: | ||
| + | * '''Minimum Length of User Passwords''' - Recommended to be at least 8 digits in length. | ||
| + | * '''Minimum Number of Upper Case Characters In Password''' - Recommended to include at least one upper-case character. | ||
| + | * '''Minimum Number of Numeric Characters In Password''' - Recommended to include at least one numeric character. | ||
| + | * '''Minimum Number of Non Alpha-numeric Characters (_:!&()?-@,.+) in Password''' - Recommended to include at least one special character. | ||
| + | * '''Maximum Number of Identical Consecutive Characters In Password''' - Recommended to be set to two. | ||
| + | * '''Allow User's System Username In Password''' - Recommended to not allow user names in the password. | ||
| + | * '''Allow User's Real Name In Password''' - Recommended not to allow a persons real name to be used in a password. | ||
| + | * '''Allow Organisation Name In Password''' - Recommended not to allow the organisations name to be used in a password. | ||
| + | * '''Allow Browser to Save Username and Password''' - This tells the browser that the password is not to be saved (stored) on the local machine (this is ignored by some browsers). | ||
| + | * '''Do not allow the reuse of previous Passwords''' - Recommended that at least 10 different passwords variations should be used before re-using a previous password. | ||
| + | * '''Number of Days Before User Password Change Required''' - This is recommended to be set to a period between 30 and 90 days. | ||
| + | |||
| + | Password security is essential to protect the data in the system. The above are general reconsiderations, however making passwords too secure can also threaten security. If passwords are made to be too complicated for users to remember, there is a high chance that the user may be tempted to write them down (or even attach them to their monitor or underside of their keyboard). | ||
Revision as of 11:16, 6 March 2019
The system has a host of security features as standard with a wide range of additional options. On this page you will find details of features and guides to make you system even more secure.
In this section you will find features related to the general access of the system.
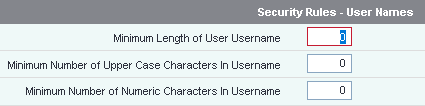
User name rules
This feature is planned to be replaced with the use of email addresses for users.
At present you can force user names to have a minumum length, to include upper-case characters and numbers.
To use this feature please see Operational Rules.
Password rules
The system can force users to use secure complex passwords. This will reduce chance of passwords being guessed by unauthorised people. Password rules are also used to protect against 'Brute Force Attacks' (when a combination of characters for the user name and password are entered until access is granted).
The following rules are available:
- Minimum Length of User Passwords - Recommended to be at least 8 digits in length.
- Minimum Number of Upper Case Characters In Password - Recommended to include at least one upper-case character.
- Minimum Number of Numeric Characters In Password - Recommended to include at least one numeric character.
- Minimum Number of Non Alpha-numeric Characters (_:!&()?-@,.+) in Password - Recommended to include at least one special character.
- Maximum Number of Identical Consecutive Characters In Password - Recommended to be set to two.
- Allow User's System Username In Password - Recommended to not allow user names in the password.
- Allow User's Real Name In Password - Recommended not to allow a persons real name to be used in a password.
- Allow Organisation Name In Password - Recommended not to allow the organisations name to be used in a password.
- Allow Browser to Save Username and Password - This tells the browser that the password is not to be saved (stored) on the local machine (this is ignored by some browsers).
- Do not allow the reuse of previous Passwords - Recommended that at least 10 different passwords variations should be used before re-using a previous password.
- Number of Days Before User Password Change Required - This is recommended to be set to a period between 30 and 90 days.
Password security is essential to protect the data in the system. The above are general reconsiderations, however making passwords too secure can also threaten security. If passwords are made to be too complicated for users to remember, there is a high chance that the user may be tempted to write them down (or even attach them to their monitor or underside of their keyboard).